Red Hat Advanced Cluster Security for Kubernetes
Containers and microservices have initiated a significant transformation in application infrastructure, and Kubernetes has emerged as one of the most rapidly adopted technologies, helping organizations automate the management of these foundational elements of applications. This major shift in infrastructure has led to a parallel transformation in security.
In today’s Kubernetes world, you need a security platform that protects your entire environment.
Red Hat Advanced Cluster Security for Kubernetes (RHACS) is a comprehensive solution designed to provide security and compliance in Kubernetes environments. It is a leading Kubernetes-native security platform that enables organizations to build, deploy, and run cloud-native applications more securely. This review will focus on the key features of RHACS, evaluating the overall performance and security capabilities the product provides.
Architecture and Integration
RHACS is designed with an architecture to provide effective security in Kubernetes environments. This solution offers deep integration with Kubernetes APIs, ensuring the comprehensive protection of the containerized environment. Additionally, it provides seamless integration with the extensive Red Hat ecosystem, ensuring compatibility with existing infrastructures.
Comprehensive Security Audits
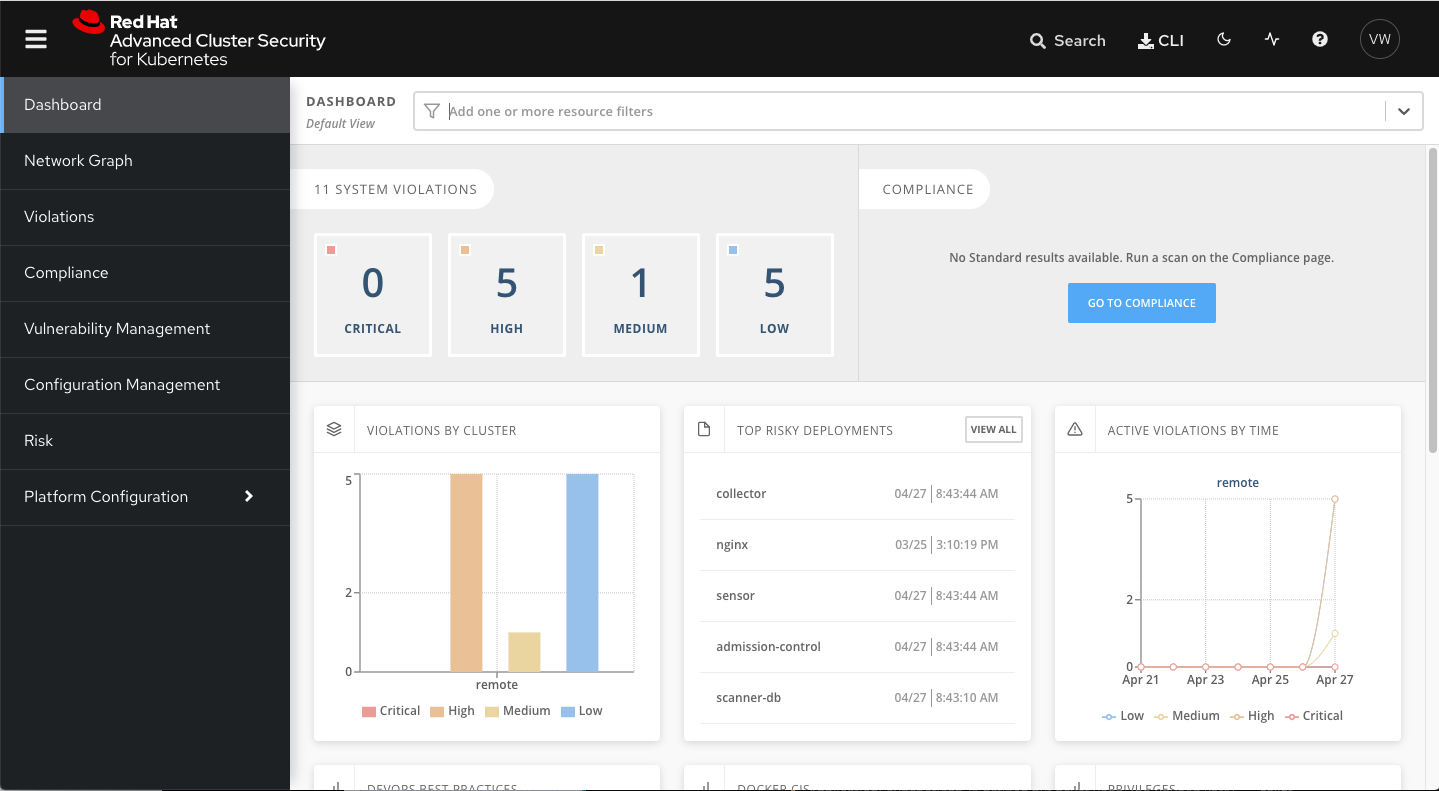
RHACS provides comprehensive security audits. It utilizes advanced threat detection technologies to identify potential security vulnerabilities at runtime, during image creation, and during deployment of containers. This capability enables the security team to respond quickly and prevent potential threats.
Policy Management and Enforcement
RHACS provides a user-friendly interface for defining and enforcing security policies. Security teams can create customized policies and easily manage their implementation. This allows organizations to configure their settings in a way that aligns with specific security requirements.
Vulnerability Analysis and Security State Monitoring
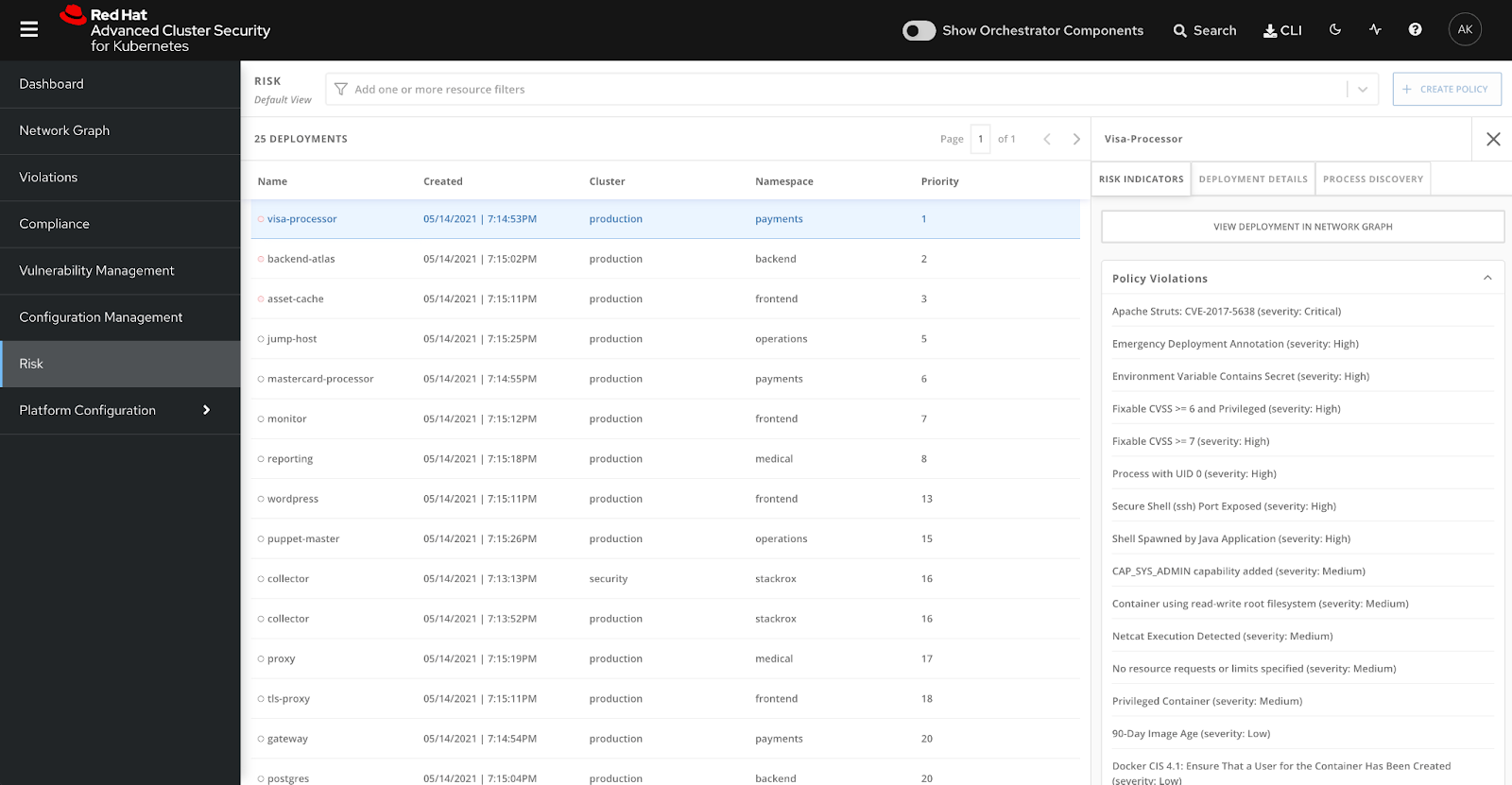
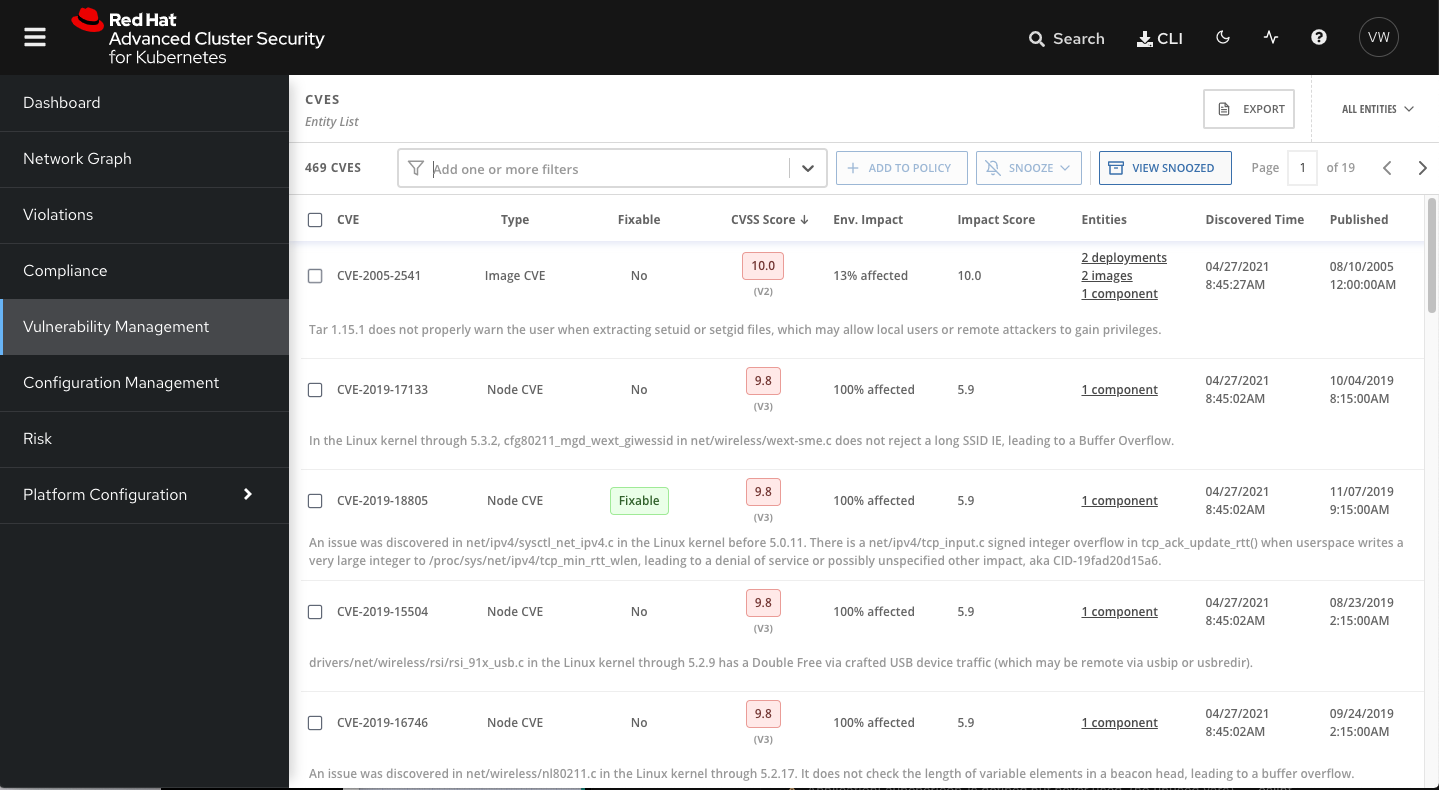
RHACS boasts robust features for vulnerability analysis and security state monitoring. By detecting critical security vulnerabilities and compliance violations, it enables organizations to swiftly intervene. Additionally, it offers the capability to centrally manage event logs and monitoring data.
Automatic Response and Protection
RHACS is equipped with automatic response mechanisms and intrusion detection systems. These features minimize security vulnerabilities by swiftly detecting attacks and automatically applying countermeasures.
Training and Support: Red Hat provides comprehensive training and support to its users. RHACS users can optimize their security strategies by adopting the product agilely and using it effectively.
Features and Benefits
Lower Operational Costs
Reduces operational costs of team silos by directing development, operations, and security teams towards a common language and a real source.
Utilizes Kubernetes native controls at the application’s build, deploy, and run stages for better visibility and management of security vulnerabilities, policy and configuration violations, and application runtime behavior.
Reduces the cost of identifying and fixing a security issue by catching and resolving it in the development stage.
Reduce Operational Risk
Aligns security and infrastructure to reduce application downtime using built-in Kubernetes features such as Kubernetes network policies and the admission controller for the enforcement of security policies for segmentation.
Mitigates threats by applying security policies using Kubernetes native security controls, minimizing potential impacts on your applications and infrastructure operations.
Increase Developer Productivity
Leverage Kubernetes and existing continuous integration and continuous delivery (CI/CD) tools to provide integrated security guardrails that support developer speed while maintaining the desired security posture.
Standardize Kubernetes as a common platform for notification-based and continuous security across development, security, and operations, increasing your organization’s innovation speed and providing actionable guidance to developers.
Benefits
Red Hat Advanced Cluster Security for Kubernetes offers a robust and comprehensive option for organizations seeking a security-focused Kubernetes solution. With high-level security controls, automatic response mechanisms, and a user-friendly interface, RHACS provides significant advantages to organizations in securely managing Kubernetes environments.
